 Western Ukraine power company Prykarpattyaoblenergo reported an outage on December 23 2015, saying the area affected included regional capital Ivano-Frankivsk, with a population of 1.4 million, during few hours.
Western Ukraine power company Prykarpattyaoblenergo reported an outage on December 23 2015, saying the area affected included regional capital Ivano-Frankivsk, with a population of 1.4 million, during few hours.
Now at January 2016, the researchers have proof that link that outage with the malware called BlackEnergy.
BlackEnergy is a popular malware that is sold in the Russian cyber underground and dates back to early as 2007.
Originally, it was designed as a toolkit for creating botnets for use in conducting Distributed Denial of Service (DDoS) attacks; but over the time has evolved to support different plugins, which are used to extend its capabilities to provide necessary functions, depending on the purpose of an attack.
The BlackEnergy toolkit capabilities has been used by different gangs for different purposes like sending spam, stealing banking credentials; but the most notorious use may be when it was used to conduct cyberattacks against Georgia during the Russo-Georgian confrontation in 2008, also at the summer of 2014, BlackEnergy was tailored by plugins to target Ukrainian government institutions.
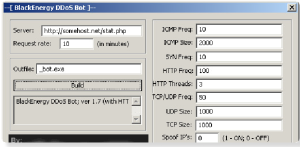
The BlackEnergy toolkit comes with a builder application which is used to generate the clients that the attackers use to infect victim machines; also it comes with server-side scripts, which the attackers set up in the Command and Control (C&C) server. The scripts also provide an interface where an attacker can control his bots. The simplicity and convenience provided by this toolkit means that anyone who has access to the kit can build his own botnet without any skills required, and how was demonstrated by the Ukraine power grid attack it can be easily converted in a cyber weapon.
In order to do the Ukraine power outage was used the BlackEnergy’s trojan, together with a backdoored SSH server introduced in the targets’ system and the destructive KillDisk plugin, which were all detected in several electricity distribution companies in Ukraine, are a dangerous set of malicious tools used as cyber weapon that give the attackers remote access to the company’s network and the capability of shutting down critical systems and by wiping their data, making it harder to get them up and running again.
But how is possible that “standard” malware can infect specialized industrial software?

It’s common, in order to reduce cost and time, that dedicated software used to program and control industrial hardware will run on PCs with operating systems like Windows or Linux; and these can then be targeted using similar or even the same malware that is used to attack regular internet users; and also all the regular vectors of attack can be used, including human error and social engineering.
Another very serious risk is to connect industrial systems to the internet, but based on my expertise this practice is common due to practicality and cost savings, because in order to reduce the number of high level trained employees is allowing to the existent ones to access the system remotely and solve any problem in an expedite way.
This factors of integrating commercial solutions and internet connection exposes the industrial control system to the same threats that common PCs face, but with much fewer options for defense because for example, software patching is much more problematic with industrial systems because they tend to be heavily customized and they are often always on, and in order to perform a maintenance it must be very well planned.
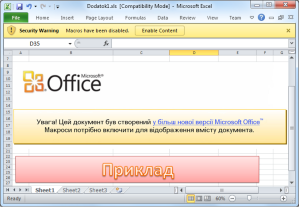
At the Ukraine power attack, the vector used was to convince the user to execute a malicious macro in Microsoft Office files. In this case no vulnerability is used to try to infect system, just trying to trick the user to execute the malicious macro.
But BlackEnergy is not the first cyber weapon known because at January 2010, the most sophisticated cyber weapon the world had ever seen, ravaged the Iran’s nuclear program.
This malware dubbed Stuxnet, was allegedly developed by the U.S. and Israel to infect the Natanz uranium enrichment plant in Iran, the complex virus infected the computer system that ran the centrifuges and making slight tweaks to the software caused hundreds of the centrifuges to self-destruct.

Stuxnet was designed to manipulate computer systems made by the German firm Siemens that control and monitor the speed of the centrifuges. The attack was due by infecting the Step 7 project files used to program Siemens’ PLCs.
The computers at Natanz are disconnected from the internet and cannot be reached directly by the remote attackers. Because this Stuxnet was designed to spread via infected USB flash drives using the Windows Autorun feature or through the victim’s local network using the print-spooler zero-day exploit that Kaspersky Lab and Symantec later found in the code.
In order to Stuxnet reach its target machines, the attackers first infect computers belonging to five outside companies that are believed to be connected in some way to the nuclear program. Then employees from this companies become an unwitting courier who will help spread and transport the weapon on flash drives into the protected facility and the Siemens computers at the end.
It’s not clear how long it took Stuxnet to reach its target after infecting machines in the contractor companies.
According to one U.S. intelligence source, Stuxnet’s developers tried to deploy a version of the Stuxnet malware to attack North Korea’s nuclear weapons.
This malware would be activated when it encountered Korean-language settings on an infected machine.

The attackers could not access the core machines that ran Pyongyang’s nuclear weapons program as was at Iran, and tried to deploy it using the same vector attack; but ultimately this attempt failed because in contrast to Iranians that access the Internet broadly and had interactions with companies from around the globe; North Korea has some of the most isolated communications networks in the world, where just owning a computer requires police permission, and the open Internet is unknown except to a tiny elite. Also the country has one main conduit for Internet connections to the outside world, through China allowing the complete control over the information that pass-through it.
The advantage that custom-made have over a weaponized public-domain malware, reside in the firsts are more difficult or impossible to detect by commercial antivirus because the limited and targeted objectives prevent to this companies get samples to be incorporated in their solutions before the attack was did. But the use of public domain malware for politically-oriented attack is an intriguing convergence of criminal activity and espionage, because as the kit is being used by multiple criminal groups, it provides a greater measure of plausible deniability than is afforded by a custom-made piece of code.
Julian Bolivar-Galeno is an Information and Communications Technologies (ICT) Architect whose expertise is in telecommunications, security and embedded systems. He works in BolivarTech focused on decision making, leadership, management and execution of projects oriented to develop strong security algorithms, artificial intelligence (AI) research and its applicability to smart solutions at mobile and embedded technologies, always producing resilient and innovative applications.
BlackEnergy and Stuxnet the first Cyber Weapons on a Global Cyberwarfare
No comments:
Post a Comment