 Quantum computing is a new way to build computers that takes advantage of the quantum properties of particles to perform operations on data in a very different way than traditional computers.
Quantum computing is a new way to build computers that takes advantage of the quantum properties of particles to perform operations on data in a very different way than traditional computers.
With this computational performance improvement came other risks, and more in the cryptography area where the security resides in apply to the plain data mathematical operations hard to replicate in a reasonable time without the knowledge of specific parameters values.
At quantum computers exist the Shor’s algorithm and the Minimization algorithm can efficiently factor numbers and can break RSA, Diffie-Hellman and other discrete log-based cryptosystems, including those that use elliptic curves.

The Shor’s algorithm is composed of two parts. The first part of the algorithm turns the factoring problem into the problem of finding the period of a function, and may be implemented classically. The second part finds the period using the quantum Fourier transform, and is responsible for the quantum speedup.
Minimization algorithm relies on first transforming the factorization problem into an optimization problem and as was exposed at my other article “Quantum Computers are already here? “, at the level of the machine, the actual quantum processor solves a Quadratic Unconstrained Binary Optimization problems that can provide faster ways to get optimal and semi-optimal results.

Before have panic and declare that internet security is broken, we need to know using these algorithms the largest such number that we found without using any prior knowledge of the solution to the factorization problem was 56153, that is 16 bits, using only 4 qubits; in order to exploit the true power of quantum mechanics in this type of computation, finding the solution will need to make use of more qubits and remember that D-Wave 2X have 1000 qubits available to be used in the quantum processor.
In August 2015, the U.S. government’s National Security Agency (NSA) released a major policy statement on the need to develop standards for post-quantum cryptography (PQC).
 In this announcement, the NSA explain about his intentions to “initiate a transition to quantum resistant algorithms in the not too distant future” and also recommend “for those partners and vendors that have not yet made the transition to Suite B elliptic curve algorithms, we recommend not making a significant expenditure to do so at this point but instead to prepare for the upcoming quantum resistant algorithm transition.”
In this announcement, the NSA explain about his intentions to “initiate a transition to quantum resistant algorithms in the not too distant future” and also recommend “for those partners and vendors that have not yet made the transition to Suite B elliptic curve algorithms, we recommend not making a significant expenditure to do so at this point but instead to prepare for the upcoming quantum resistant algorithm transition.”
NSA Suite B Cryptography is a set of cryptographic algorithms promulgated as part of its Cryptographic Modernization Program; and It is to serve as an interoperable cryptographic base for both unclassified information and most classified information.
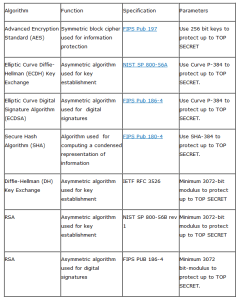
NSA Suite A Cryptography is a cryptography category which contains classified algorithms that will not be released and will be used for the protection of some categories of especially sensitive information.
Also the NSA recommend “for those customers who are looking for mitigations to perform while the new algorithm suite is developed and implemented into products”, “first, it is prudent to use larger key sizes in algorithms in many systems”; additionally, when “using layered commercial solutions to protect classified national security information with a long intelligence life should begin implementing a layer of quantum resistant protection. Such protection may be implemented today through the use of large symmetric keys and specific secure protocol standards”.
Symmetric-key encryption schemes such as AES have the property that the fastest quantum attack known for recovering a k-bit secret key takes time 2^k/2. Thus AES with 256-bit keys is believed to provide a 128-bit security level against quantum attacks, that is half the number of bits of security that it has against conventional attacks.

At Valhala Networks to secure our documents, electronic schemas and source codes we use CuaimaCrypt that is a Symmetric-key encryption algorithm and based in a theoretical (we don’t have access to a quantum computer) pre-evaluation it is quantum resilient because it dynamic structure, number of equivalent bits and algorithm’s operation.
You can use it free just downloading the “CuaimaCrypt Command Line” or CCLI from the Valhala’s web site.
Other viable candidates for postquantum cryptography can be Lattice-based cryptography that are being intensively studied by cryptographers, because they can be used to achieve fully homomorphic encryption and code obfuscation not known to be achievable using conventional RSA and discrete logarithm cryptography.

Hash-based cryptography, because is believed to have the same security against quantum computers as against conventional ones, k/2 bits of security, where k is the bit length of hash values.
Multivariate polynomial cryptography, where the security of these schemes is based on the difficulty of solving a multivariate system of polynomial equations over a finite field.
Isogeny-based cryptography, where the security of these schemes is based on the difficulty of computing an isogeny of a certain degree between two isogenous super-singular elliptic curves over Fp2
We must note that this post PQC algorithms don’t have any relation with Quantum Cryptography

Quantum Cryptography is essentially based on the usage of individual particles/waves of light (photon) over a transmission channel and their intrinsic quantum properties know as Heisenberg’s uncertainty principle to develop an unbreakable cryptosystem because it is impossible to measure the quantum state of any system without disturbing that system.
It is theoretically possible that other particles could be used, but photons offer all the necessary qualities needed, their behavior is comparatively well-understood.
Also the actual commercial quantum cryptography is used in quantum key distribution systems over fiber channels.
In conclusion I don’t think that internet security is actually broken, but the certain is, based on the actual quantum computer’s development state, in few years “we will be short” at the quantity of bits used by current cryptographic algorithms and we need to take care of this possibility from now because after will be late.
Julian Bolivar-Galeno is an Information and Communications Technologies (ICT) Architect whose expertise is in telecommunications, security and embedded systems. He works in BolivarTech focused on decision making, leadership, management and execution of projects oriented to develop strong security algorithms, artificial intelligence (AI) research and its applicability to smart solutions at mobile and embedded technologies, always producing resilient and innovative applications.
NSA Believe that Current Cryptography Algorithms Are Broken by New Quantum Computers
No comments:
Post a Comment